4.2. API L7 DoS attacks and TLS based fingerprinting¶
In this module you will examine L7 DoS attacks against API, detection based on transaction rate per second per individual client OS or browser. Each client OS or browser have got fairly unique combination of supported ciphers, TLS extensions, compressions settings and other options exposed during TLS handshake. BIG-IP is capturing those options and producing fairly unique TLS fingerprint which can be used to identify bad actors with better granularity than traditional source based approach. The environment is already preconfigured for this use case.
4.2.1. Examine protected API environment¶
- Go to Postman, expand TLS_fingerprint collection and rapidly run List Departments API call a few times - you should be able to get blocking response from BIG-IP
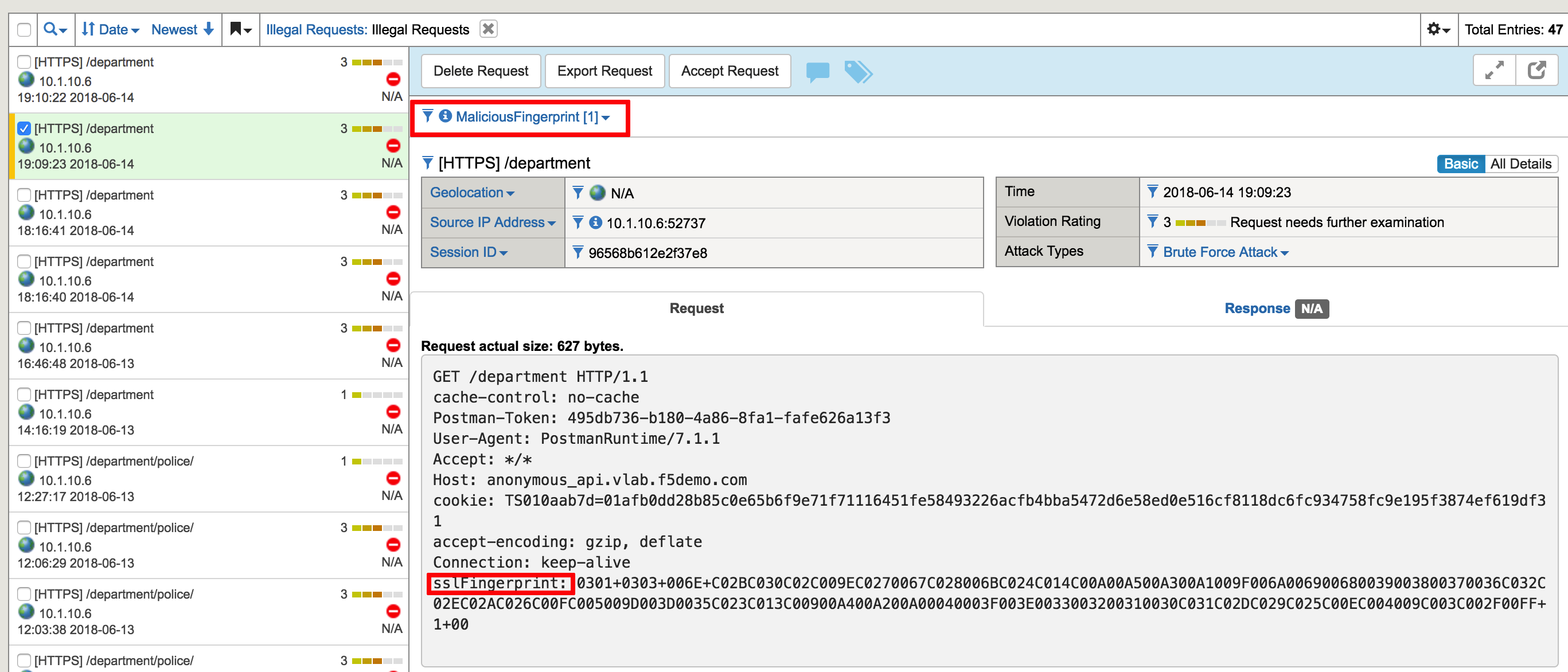
- In the BIG-IP GUI navigate to Security -> Event Logs -> Application - Requests and examine the last log message; Note violation type and TLS fingerprint
- Open the browser and access https://anonymous_api.vlab.f5demo.com/department - quickly update the page a few times to get the blocking response
- In the BIG-IP GUI navigate to Security -> Event Logs -> Application - Requests and examine the last log message; Note the difference between TLS fingerprint from Postman and web browser