3.3. Illegal Content Type Protection¶
In this module you will examine security controls for checking allowed content type within API calls. You will use Postman client to simulate API call with illegal content-type. If you are using prebuilt objects proceed to policy validation. Keep in mind, you will have to use objects with prebuilt suffix.
3.3.1. Examine unprotected API environment¶
- Launch Postman application
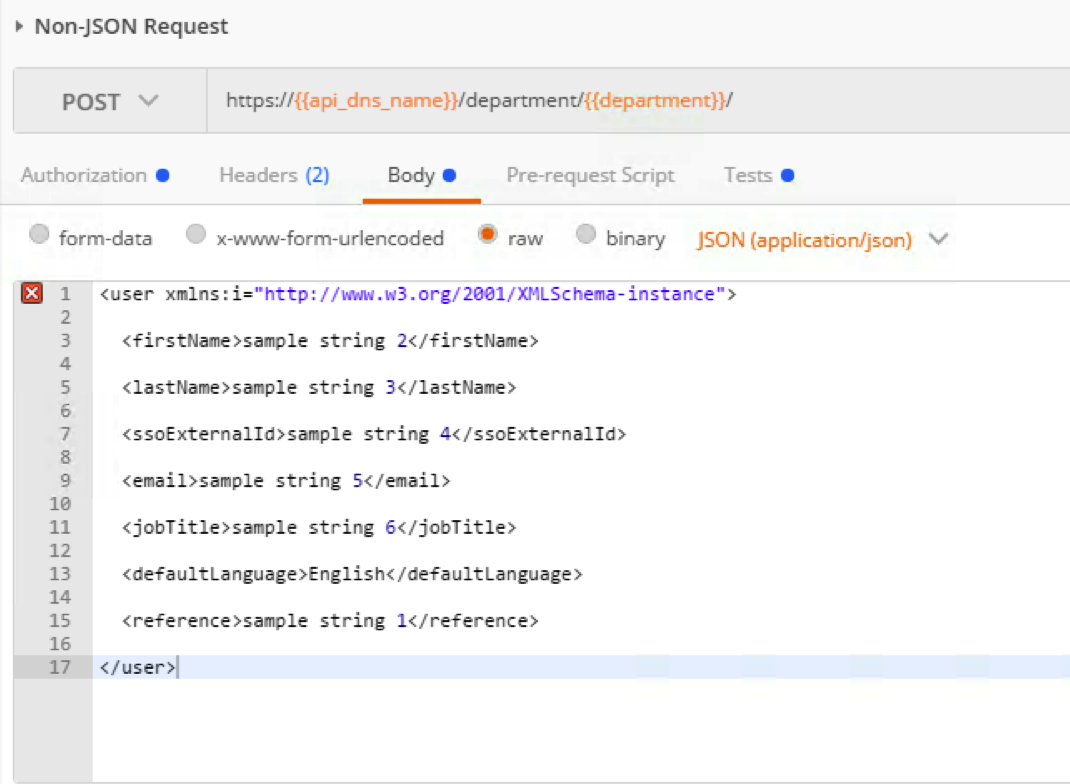
- Click Collections -> HR_API_Illegal -> Non-JSON request. Click Body and examine the payload of API POST call
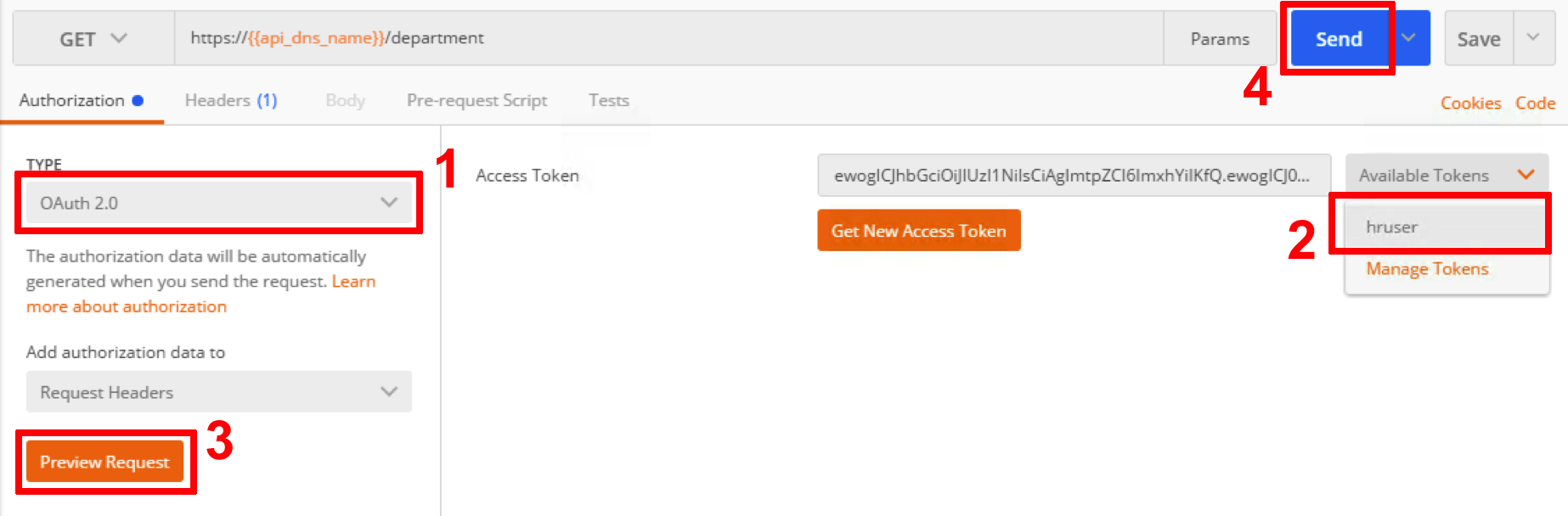
- Make sure authorization type is set to OAuth 2.0. From the list of available tokens select hruser and click Preview Request. Then click Send
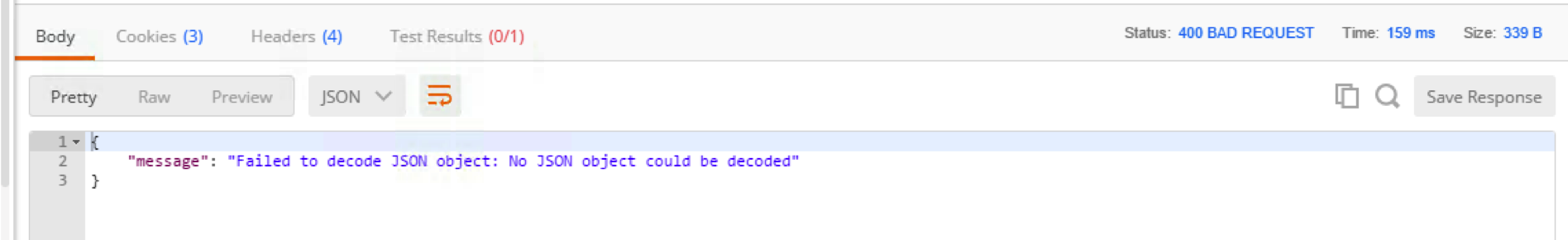
- Examine the output
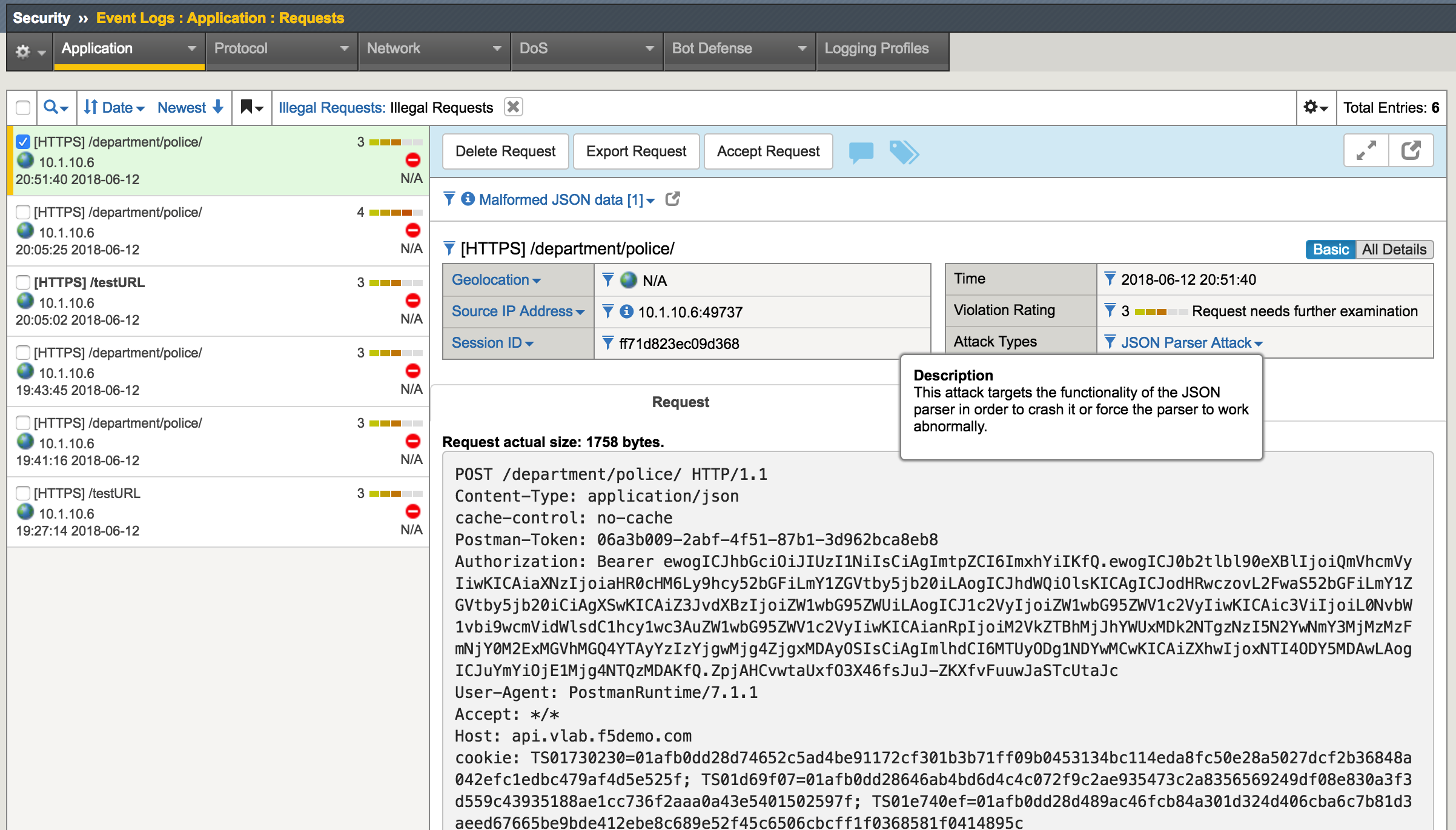
At this time we don’t have any specific security policy related to illegal content type, so the API call is expected to come through. API server is not able to decode non-JSON payload.
3.3.2. Illegal content type protection configuration¶
- In the BIG-IP GUI go to Security -> Application Security -> URLs —> Allowed URLs -> Allowed HTTP URLs
- Click on /department*
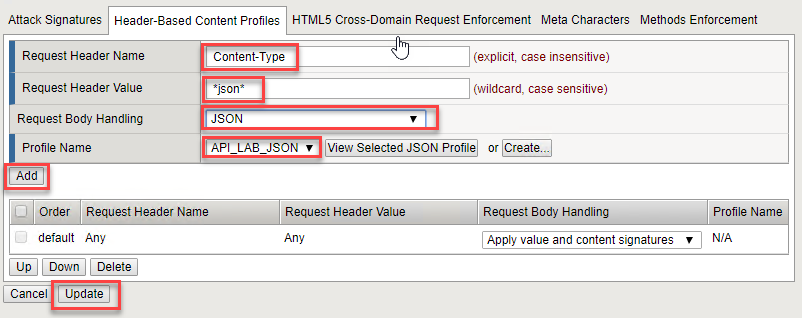
- Select Header-Based Content Profiles tab and define Content-Type in the Request Header Name form
- In the Request Header Value form specify *json*
- In the Request Body Handling dropdown menu select JSON and in the Profile Name specify API_LAB_JSON
- Click Add, Update and Apply Policy
3.3.3. Validation¶
- Go back to Postman and run Non-JSON request again - this API call should be blocked
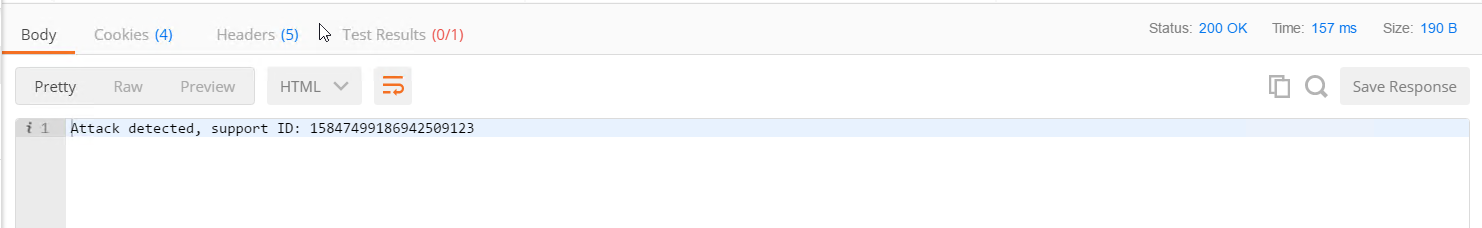
- In the BIG-IP GUI to Security -> Event Logs -> Application - Requests and examine the last log message