3.5. Attacks mitigation¶
In this module you will examine security controls allowing to protect against known attack patterns against API infrastructure. If you are using prebuilt objects proceed to policy validation. Keep in mind, you will have to use objects with prebuilt suffix.
3.5.1. Examine unprotected API environment¶
- Launch Postman application
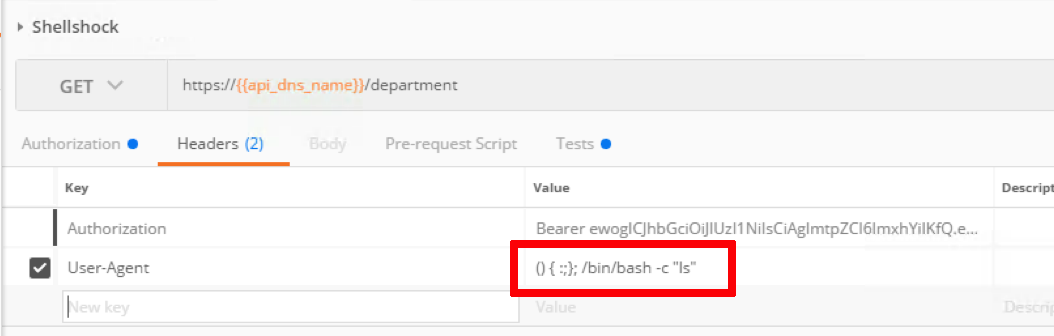
- Click Collections -> HR_API_Illegal -> Shellshock. Click Headers and examine the value for User-Agent
This string is trying to exploit well known vulnerability CVE 2014-6271 also known as Shellshock
https://cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2014-6271
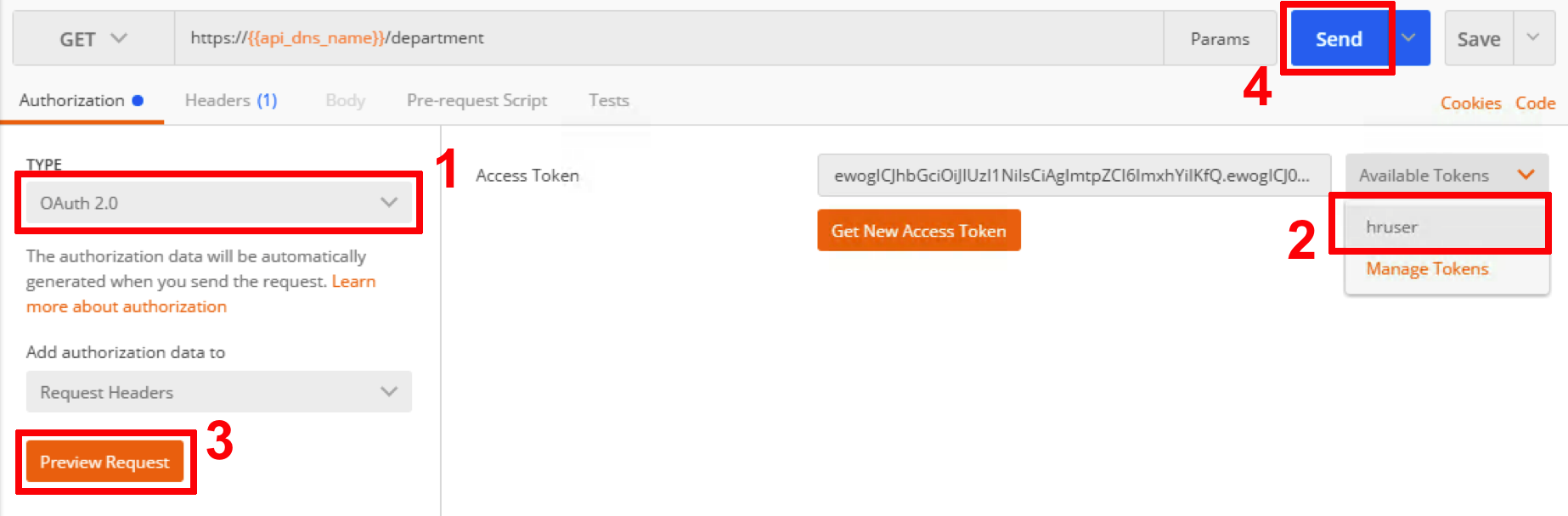
- Make sure authorization type is set to OAuth 2.0. From the list of available tokens select hruser and click Preview Request. Then click Send
- The API call is able to come through along with remote command execution embedded into User-Agent string
3.5.2. Attacks protection configuration¶
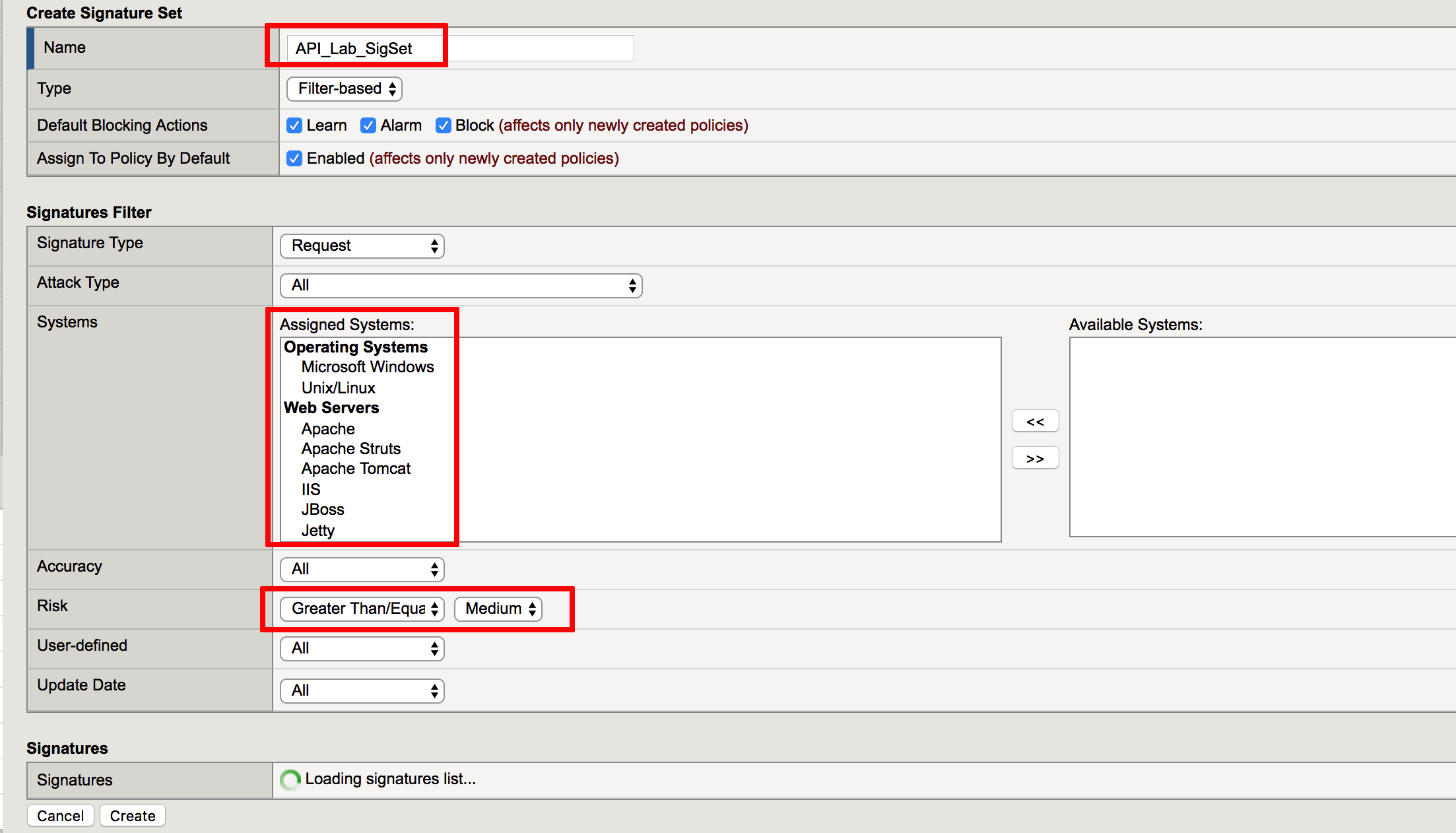
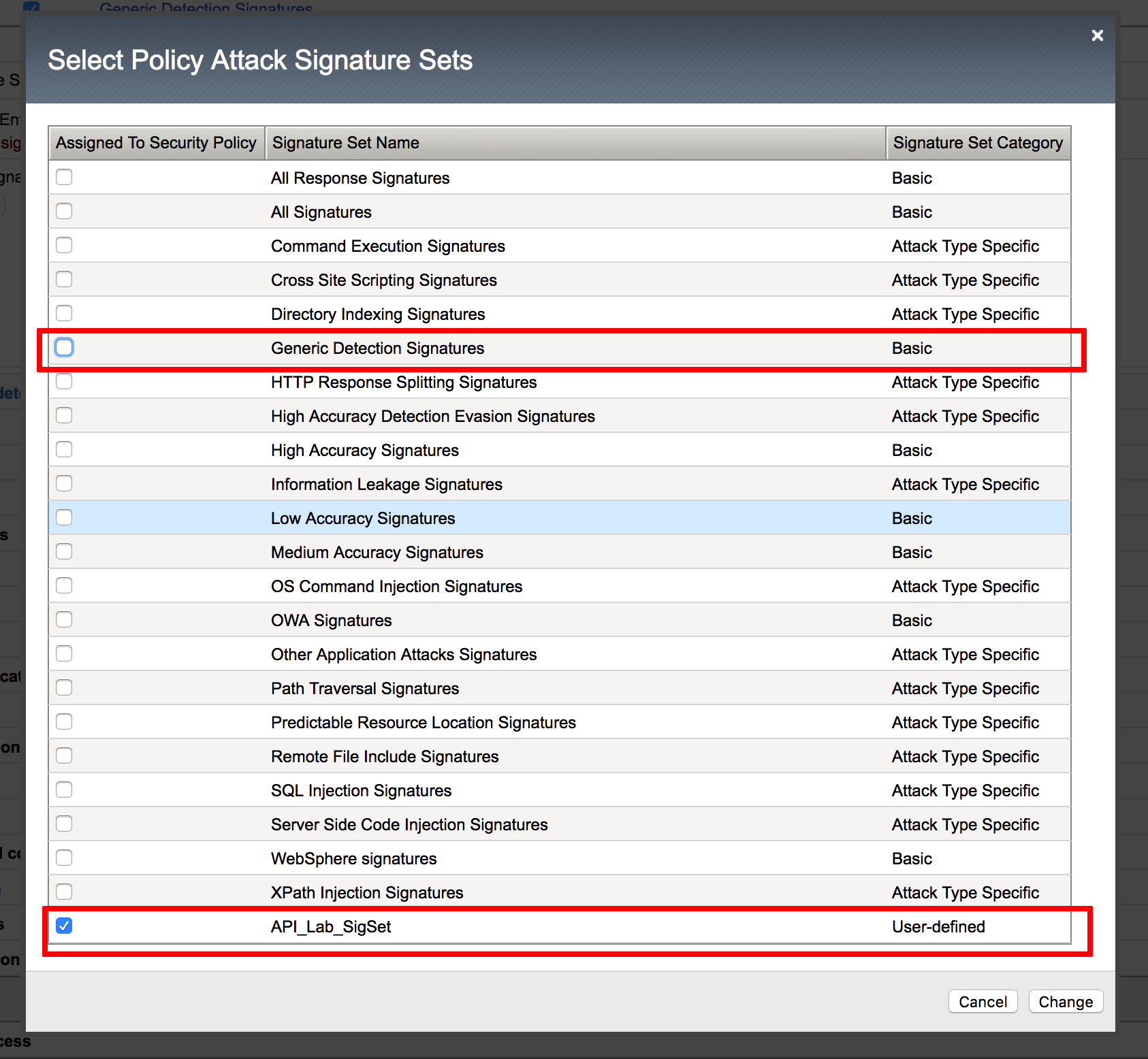
- In the BIG-IP GUI navigate to Security -> Options -> Application Security -> Attack Signatures -> Attack Signature Sets
- Tap Create, define a name API_Lab_SigSet2, select all items in the Available Systems list and move it into Assigned Systems. Specify Risk as Greater Than/Equal Medium and tap Create
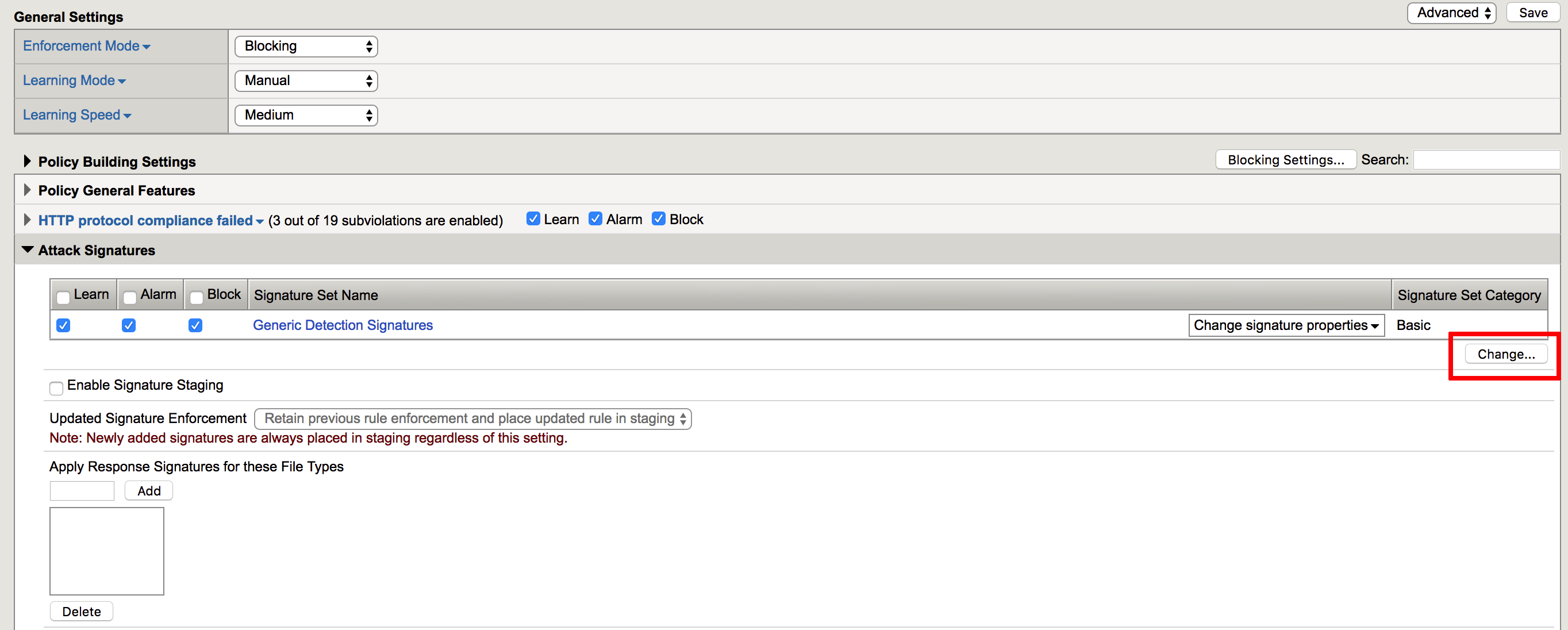
- Navigate to Security -> Application Security -> Policy Building -> Learning and Blocking Setting, expand Attack Signatures section and click Change
- Uncheck Generic Detection Signatures and check API_Lab_SigSet, then click Change, Save and Apply Policy
You can choose the prebuilt set or the set you just created.
3.5.3. Validation¶
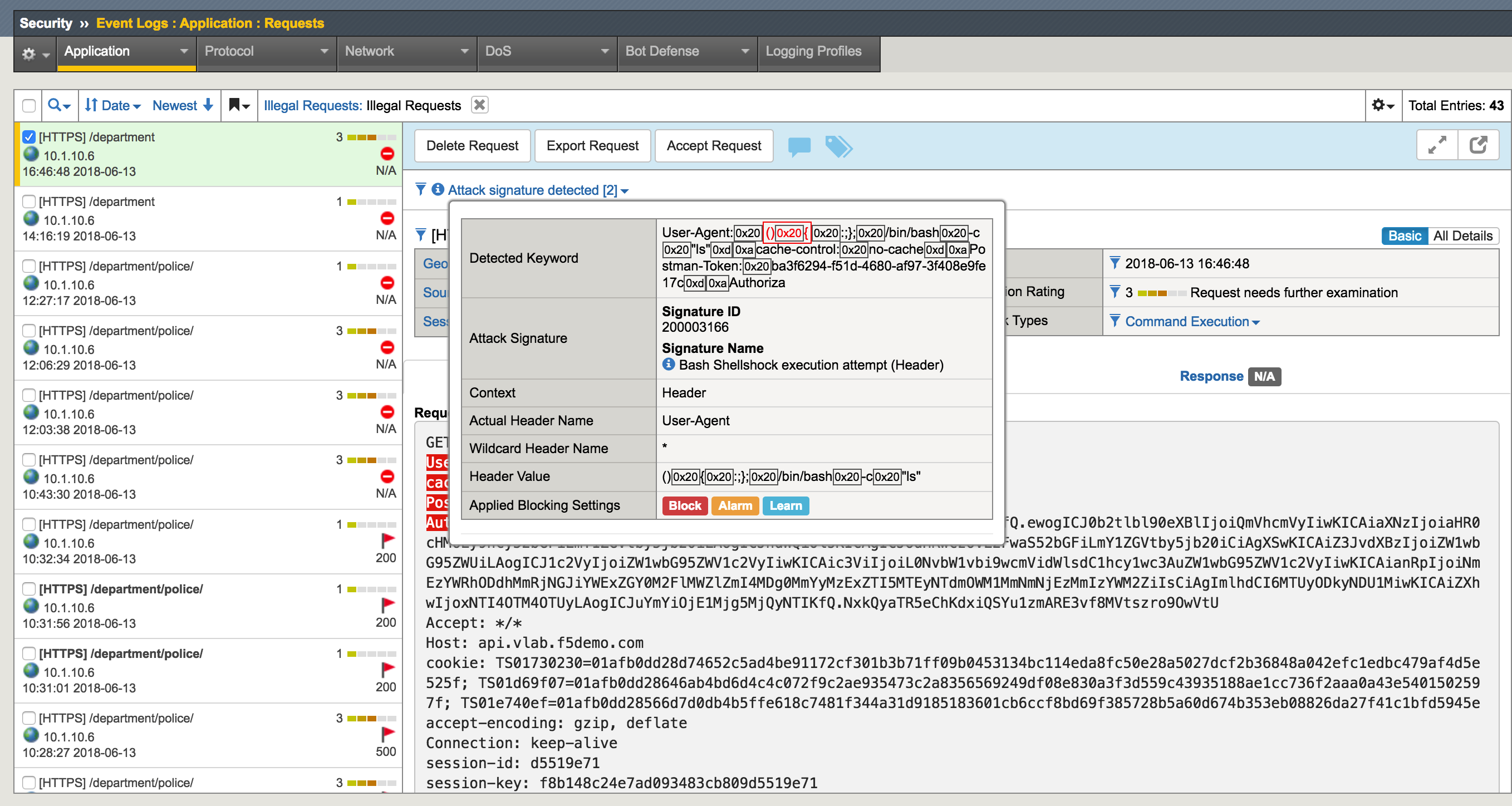
- Go back to Postman and run Shellshock API call again - the API call should be blocked
- In the BIG-IP GUI to Security -> Event Logs -> Application - Requests and examine the last log message
API call is matching the signature and hence being blocked